The Great Identity Debate at the Internet2 Global Summit 2017 saw experts in the identity field debate a fundamental question for our community. The panel was asked to debate for and against this proposal:
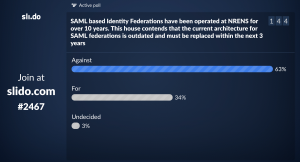
SAML based Identity Federations have been operated at NRENS for over 10 years. This house contends that the current architecture for SAML federations is outdated and must be replaced within the next 3 years.
This was of course somewhat of a tongue-in-cheek debate and a response to the “SAML is dead” dialogue, as all of the panel work happily with SAML in the identity management community. As Brook pointed out in the session, it often sounded like at least 5 of the panelists were on his team! Nevertheless, the participants identified and discussed some important issues that are often raised regarding SAML and its use by research and education federations.
Old Tech / New Tech
Arguments have been made that SAML is now “old’ technology and should be replaced with more modern alternatives, such as OpenID Connect, or indeed Blockchain.
OIDC was developed in part because SAML is seen as being very complicated. However, as OIDC and its underlying technologies evolve to meet the same use cases, we’re seeing it develop towards the same level of complexity that SAML currently enjoys. OIDC is not better, it’s just different. If you want OIDC to remain a lighter weight service, you should consider using it with use cases that don’t require the level of complexity that SAML supports. These environments don’t have to be mutually exclusive. In some cases, the attributes (or claims) hardly matter; so, don’t require SAML support in those cases.
The state of the technology is still evolving; a full shift to OIDC before we actually have a way to fully support an OIDC federation is not a good idea. SAML may have been around for a while, but then so have a lot of the technologies we rely on everyday – like DNS. Maturity is a good thing in the services we fundamentally rely on everyday. This doesn’t mean we have to standstill and the R&E envrionment is growing – eduGAIN recently announced a move to a technology agnostic policy framework in order to allow new and different technologies to take advantage of its well established trust framework.
User Experience
The user experience of SAML has come in for some fair criticism – the “where are you from” or IdP discovery process is often poorly implemented and has translated badly to mobile devices. REFEDS has long promoted best practice in this area, but has not seen much uptake of its recommendations…but is this enough to push for a change in technological approach?
One of the complexities and added values of the existing SAML federations is that the IdPs hold verified information about the user which only they can assert. Finding a way to insert this information into a workflow between user and service is always going to be challenging from a user interface perspective.
We also need to think about how we are supporting implementers. The world of commercial entities, such as scholarly publishers, that support federated identity is way behind where much of academia seems to be – the recent work by the RA21 project suggests those commercial entities are just getting on the SAML bandwagon now. We are at the lead of federated identity; do we really want to shift gears before providers of services can catch up?
Security and Privacy
The changing security and privacy requirements may present a good reason to reevaluate which technologies we are using and how we are implementing them. At the Internet2 Global Summit we repeatedly heard from US colleagues who had been spending a lot of time looking at the new European General Data Protection Regulation (GDPR), clearly understanding the impact that this will have outside of Europe as well as within. Identity Federations and their members continue to struggle with the duelling requirements of keeping user data secure but also ensuring that attributes do get released in appropriate circumstances. Consent has become a thorny issue (and could easily be the next Great Identity Debate): is consent the holy grail that brings clarity to all attribute exchange permissions, or an excuse to push the problem back on the user? Can consent ever be freely given when data must be released to use a resource?
However a change in approach will not make these issues go away and could conversely take us back several steps in terms of our ability to meet the challenges of data protection.
Trust Architecture
Most of the panelists eventually agreed on one thing: at the end of the day the technologies we use are less important than the trust fabric that we build. R&E has been very successful in building up a trusted environment with significant numbers of IdPs and SPs participating in that environment – MET currently shows 13638 entities within federations across the globe. Maintaining a trust architecture that is fit for purpose is the main priority of all federations now, in 3 years and for the foreseeable future.
In the end the “Against” team won and I admitted defeat to Brook’s debating team – but the session help identify some really important perceptions that identity federations need to manage as we move forward. With thanks to Maarten Kremers, Jacob Farmer, Tom Siu, Heather Flanagan, Leif Johansson and Rhys Smith for bravely accepting our challenge to debate!